vmware
Make vmexplorer.com great again!
 It’s that time of year to vote for your favorite virtualization blog on vSphere-Land.com For those that don’t know. vSphere-Land is a great resource for VMware virtualization information. Mainly this site is known for various lists around VMware products and information. Every year they host a voting session to help promote the VMware blogging community. Soon after the voting concludes vSphere-Land post the TOP vBLOGs for 2017. This list helps to support the hard work bloggers do to support VMware community.
It’s that time of year to vote for your favorite virtualization blog on vSphere-Land.com For those that don’t know. vSphere-Land is a great resource for VMware virtualization information. Mainly this site is known for various lists around VMware products and information. Every year they host a voting session to help promote the VMware blogging community. Soon after the voting concludes vSphere-Land post the TOP vBLOGs for 2017. This list helps to support the hard work bloggers do to support VMware community.
Also, new this year voters must pick 12 blogs from the list then rank them. They also will have a choice to choose in various categories (Top Female blog, best podcast, etc) This task can be a bit overwhelming and if you are struggling to find twelve blogs I would suggest looking at some of the blogs and seeing which ones align better to your goals. Example — If you’re into scripting I might suggest William Lam’s Blog, or for vSAN maybe Cormac Hogan.
Why Vote for vmexploer.com? I’ve run this blog since 2010 and have helped countless amounts of IT folks along the way. If you’ve found any of my blogs useful over these past years then I would appreciate a vote and with 12 to choose from please include vmexplorer in your list. Vote for vmexplorer as #1 would even be better. The list of blogs to choose from can be a bit daunting, best way to find mine is to do a page search for my last name or blog name vmexplorer.com
To Vote, simply start by going to this link — http://topvblog2017.questionpro.com/
Voting will close on 06/30
Again, thank you for your support and I’m looking forward to more years of blogging!
vSAN – Working with the vSAN HCL Database
The vSAN HCL DB is a local file enabling vCenter Server to validate your vSAN hardware deployment. This local DB file contains information around the supported products on the VMware compatibility guides. Part of the vSAN Health checks is validating the age of the vSAN HCL DB file. The initial release of the health feature ships with a copy of the vSAN HCL DB, which was current when released. This copy of the database will become outdated over time. The file can be updated via an internet connection or through manual download (See KB’s below). However, if the HCL DB file is not updated and is 90 days past you will see a warning and at 180 days past you’ll receive an error. These alerts in no way will affect your vSAN cluster as they are merely non-impactful alarms.
You can find this check by clicking on your vSAN Cluster > Monitor > Virtual SAN > Health and then expand Hardware compatibility (See the PIC below). Under Hardware compatibility, you will see various checks that validate your installation. The ‘vSAN HCL DB up to date’ is the check that will alarm when needed.
You might be thinking –
“I validated my vSAN deployment against the HCL & VCL’s when it was initially built, so why do I need to recheck it over and over?” There are a few good reasons why this validation is important. First off – New firmware and drivers are validated on a routine basis, keeping on top of these will help to ensure your vSAN cluster is able to work optimally and is less problematic. Second – Just because a component was listed on the VGC, doesn’t necessarily mean it will stay on the VGC. Allowing vSAN to self-check itself not only will save you time but will identify any potential issues.
“My vSAN cluster doesn’t have an internet connection and I am pretty good about keeping up to date on the VGC. Do I really need these checks, and if not how can I disable them” Frist off I would not recommend disablement but there may be a need for this. It could be very true that your company does a good job of manually checking the VCG but automating these check would only help your efforts and would be more efficient. However, there are some deployments where automated checks may not be desirable. For those cases follow this guidance to disable: Cluster > Manage > Virtual SAN > General > Internet Connectivity > Disable Auto HCL update
For more information around the vSAN HCL DB, including how to disable and update, please see the following KB’s
- vSAN Health Service – Hardware compatibility – vSAN HCL DB Auto Update (2146132) << Great information on disablement
- vSAN Health Service – vSAN HCL Health – vSAN HCL DB up-to-date (2109870) << Good information on the checks basic functions
In this PIC I’m showing where you can locate the vSAN HCL DB Check status.

If you like my ‘no-nonsense’ blog articles that get straight to the point… then post a comment or let me know… Else, I’ll start writing boring blog content.
VSAN – vSAN 6.6 Release resources
Here is a great list of vSAN 6.6 release resources. Enjoy!
Quotes / Webinars:
- Press Release Partner Quotes Supporting Launch: http://www.vmware.com/company/news/releases/vsan-partner-quotes.html
- On-demand Launch Video – Registration Link: Modernize Your IT with vSAN Innovations
- VMUG Webinar: What’s New Technical Deep dive (Tuesday, April 18, 2017)
Blogs:
- What’s New Blogs: https://blogs.vmware.com/virtualblocks/2017/04/11/whats-new-vmware-vsan-6-6/
- Native Data-at-Rest Encryption: https://blogs.vmware.com/virtualblocks/2017/04/11/vsan-6-6-native-data-at-rest-encryption/
Web Assets / Documentation :
- What’s New Page: http://www.vmware.com/products/whats-new-virtual-san.html
- vSAN 6.6 Datasheet (PDF): http://www.vmware.com/content/dam/digitalmarketing/vmware/en/pdf/products/vsan/vmware-virtual-san-datasheet.pdf
- vSAN Customer Page: http://www.vmware.com/products/virtual-san/customers.html
- Storage Hub: https://storagehub.vmware.com/
- Security Infographic: http://www.vmware.com/content/dam/digitalmarketing/vmware/en/pdf/products/vsan/vmware-vsan66-security-infographic.pdf
VSAN – What’s new in vSAN 6.6 Video Demo
What a great video posted by Duncan and VMware! In a short 10 minute video, he is able to hit upon some of the new features within vSAN 6.6
Gigabyte MX31-BS0 Firmware / BIOS update for MergePoint Embedded Management Software and Motherboard
** Blog Updates / Notes **
I wrote this post when I first got my MX31-BS0 (2017), since then I have updated my BIOS several times using this process. Here are my notes around my most recent update experiences and blog comments.
- 07/2019 – Updated 1 host with MX-31BS0 BIOS from R10 to R11 and MergePoint EMS 8.73 to 8.85. This update didn’t go smooth and I cannot recommend it.
- Why did I update — I recently installed Java 9 and the vKVM under EMS 8.73 would not work. After installing R11/8.85 Java 9 seemed to work but I had issues
- Notes / Issues:
- Noted EMS 8.85 Changes: I didn’t dig in deep but the install log screen got a new look, and all the rest of the screens seemed to be the same. I had some random quirkiness (as stated int he blog post below) during the update, but nothing out of the ordinary.
- vKVM/vMedia Issues:
- EMS 8.85 with the vKVM or the vMedia would disconnect upon reboot of the host OR it would do this randomly. This is with the ‘Keep PHY link up’ enabled.
- Tested on a system with Java 8 and had the same results
- Downgraded to EMS 8.73 with BIOS R11 all issues went away
- I did not test EMS 8.80 or 8.83
- 09/2018 – Mix of updates for my three hosts — Updated MX-31BS0 BIOS from R03 or R08 to R10 and 2 hosts MergePoint 8.58 to 8.73, as one host was on 8.73 already
- Noted behavior:
- After BIOS update was completed the Mobo powered off vs. rebooting as with previous updates. Had to power on the mobo to complete the BIOS install. Then the mobo rebooted one more time as expected.
- Even though the Mobo had been warm booted the BIOS Version in MergePoint web interface still showed the old version. However, the Boot BIOS screen reflected the update. A full power disconnect of the Mobo and a few ‘refreshes’ of the web browser allowed the MergePoint to report R10. I did not see this behavior with the MergePoint EMS BIOS update, it promptly reported 8.73 properly.
- Noted behavior:
- 05/2018 –Updated on host to MX-31BS0 BIOS from R03 to R08 and MergePoint 8.58 to 8.73.
- Blog readers noted issues going to R08 and could not connect to vKVM, I didn’t have any issues with update. Looks like it was a JAVA 8 Update issue (See post comments for more info)
- 09/2017 – Updated MX-31BS0 BIOS from F10 to R03 and MergePoint 8.41 to 8.58.
- 03/2017 – Original update documented below. Updated MX-31BS0 BIOS from F01 to F10 and MergePoint 8.01 to 8.41.
**** Blog Post ****
You’d think by now manufactures would have a solid and concise process around updating their products. They are quick to warn users to not update their BIOS unless there is a problem and quick to state if there is a problem they usually won’t support it. This total cycle of disservice is a constant for low-end manufacturers, heck even some high server platforms have the same issues. I have these same concerns when I started to look into updating my current MX31-BS0 Motherboard (mobo).
What can soften this blow a bit? How about the ability to update your BIOS remotely? This is a great feature of the MX-31BS0 and in this blog post, I’ll show you how I updated the BIOS and the remote MergePoint EMS (MP-EMS) firmware too.
Initial Steps –
- My system is powered off and the power supply can supply power to the mobo.
- I have setup remote access to the MP-EMS site with an IP address and have access to it via a browser. Additionally, I have validated the vKVM function works without issue
- I downloaded the correct Mobo BIOS and BMC or MP-EMS Firmware and have extracted these files
- Steps below were completed on a Gigabyte MX31-BS0 from BIOS F01 > F10 and MP-EMS 8.01 > 8.41, your system may vary
1 – Access the MergePoint EMS site
Start out by going to the IP address for MP-EMS site. From the initial display screen, we can see the MP-EMS Firmware versions but not the Platform (or Mobo) BIOS Version. Why not you may ask? Well, the MP-EMS will only display Mobo information when the Mobo is powered on. Before you power on your Mobo I would recommend opening the vKVM session so that you can see the boot screen. When you power on your mobo (MP-EMS > Power > Control > Power On ) use the vKVM screen to halt at the ‘boot menu’ or even go into setup and disable all the boot devices.
In this PIC, we can see my Firmware for the MP-EMS is 8.01 and the BIOS is blank as the Mobo is not powered on.

2- Selecting the Mobo BIOS Update
I choose the following to update the Mobo BIOS. Start out by uploading the file: Update > ‘BIOS & ME’ > Choose File > Image.RBU > Upload

Once the upload is complete, click on ‘Update’ to proceed. NOTE: a warning dialog box appeared for me stating the system would be powered off to update the BIOS. Good thing I’m in the Boot Menu as the system will just directly power off with no regard of the system state

3 – Installing the Mobo BIOS Update: Be Patient for the BIOS install to complete
Once I saw the message the ‘BIOS firmware image has been updated successfully’ I then exited the browser session and vKVM . Note: I’d recommend closing the browser out entirely and then reopening a new session.

Once I restarted my vKVM and MP-EMS sessions and then powered on my Mobo. This allowed the BIOS update to continue.
Here is the patience part – My system was going from BIOS F01 > F10 and it rebooted 2 times to complete the update. Be patient it will complete.
Here is the behavior I noted:
- First Reboot – The system posted normally, it cleared the screen, and then white text stated a warning message about the BIOS booted to default settings. Very shortly after it rebooted again.
- On the 2nd reboot, it posted normally and I pressed F10 to get back to the Boot menu. I did this because next, we’ll need to update the MP-EMS firmware.
Once the system had rebooted I then refreshed my MP-EMS screen and viola there it was BIOS Version F10.

** Note – Not every time but sometimes, I would notice the MP-EMS Screen would show the old BIOS Version #. However, in BIOS the updated BIOS Version # would be present. A cold boot didn’t always fix this, but eventually the MP-EMS would update and would reflect the correct BIOS #**
4 – Selecting the MP-EMS Firmware
While the Mobo is booted and I’m in the boot menu, I went into the MP-EMS session and choose the following Update > BMC > Choose File > 841.img > upload

5 – Installing the MP-EMS firmware update
Once the file was uploaded I could see the Current and New versions. I then choose Update button which promptly disconnected my vKVM session and Status changed from None to a % Completed.
Again, be patient and allow the system to update. For my systems the % Complete seemed to hang a few times but the total process, for me, took about 10 mins.

After the update was complete, the next screen let me know the update was successful, my system did an auto-reboot. When I heard my system beep I then closed my MP-EMS session and started a new browser session.
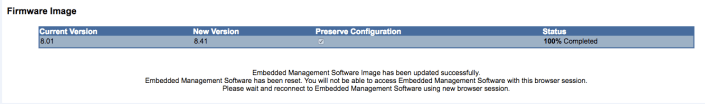
Shortly after the system booted I went into the MP-EMS and validated the firmware was now 8.41.

Wrapping this up…
Ever heard the saying “It really is a simple process we just make it complicated”? Recent BIOS updates and overall system management sometimes feel this way when trying to do simple processes. Not trying to date myself but BIOS/Firmware updates have been around for decades now. I’ve done countless updates where it was simply extracting an update to simple media and then it completes the update on its own. Now one could argue that systems are more complicated and local boot devices don’t scale well for large environments and I’d say both are very true but that doesn’t mean the process can’t be made more simple.
My recommendation to firmware / bios manufactures — invest in simplicity or make it a requirement for your suppliers. You’ll have happier customers, less service calls, and more $$ in your pocket but then again if you do, what would I have to blog about?
Am I happy with the way I have to update this Mobo? Yes, I am happy with it. For the price I paid it’s really nice to have a headless environment that I can remotely update. I won’t have to do it very often so I’m glad I wrote down my steps in this blog.
If you like my ‘no-nonsense’ blog articles that get straight to the point… then post a comment or let me know… Else, I’ll start writing boring blog content.
Home Lab Gen IV – Part III: Best ESXi White box Mobo yet?
Initially, when I decided to refresh my Home Lab to Generation IV I planned to wipe just the software and add InfiniBand. I would keep most of the hardware. However, as I started to get into this transformation I decided it was time for a hardware refresh too including moving to All Flash vSAN.
In this post, I wanted to write a bit more about my new motherboard (mobo) and why I think it’s a great choice for a home lab. The past workhorse of my home lab has been my trusty MSI Z68MS-G45(B3) Rev 3.0 (AKA MSI-7676). I bought 3 MSI-7676 in 2012 and this mobo has been a solid performer and they treated me very well. However, they were starting to age a bit so I sold them off to a good buddy of mine and I used those resources to fund my new items.
My new workhorse –
Items kept from Home Lab Gen III:
- 3 x Antec Sonata Gen I and III each with 500W PS by Antec: I’ve had one of these cases since 2003, now that is some serious return on investment
New Items:
- 3 x Gigabyte MX31-BS0 – So feature rich, I found them for $139 each, and this is partly why I feel it’s the best ESXi white box mobo
- 3 x Intel Xeon E3-1230 v5 – I bought the one without the GPU and saved some $$
- 3 x 32GB DDR4 RAM – Nothing special here, just 2133Mhz DDR4 RAM
- 3 x Mellanox Connectx InfiniBand cards (More to come on this soon)
- 4 x 200GB SSD, 1 x 64GB USB (Boot)
- 1 x IBM M5210 JBOD SAS Controller
Why I chose the Gigabyte MX31-BS0 –
Likes:
- Headless environment: This Mobo comes with an AST2400 headless chipset environment. This means I no longer am tied to my KVM. With a java enabled browser, I can view the host screen, reboot, go into BIOS, BIOS updates, view hardware, and make adjustments as if I was physically at the box
- Virtual Media: I now can virtually mount ISOs to the ESXi host without directly being at the console (Still to test ESXi install)
- Onboard 2D Video: No VGA card needed, the onboard video controller takes care of it all. Why is this important? You can save money by choosing a CPU that doesn’t have the integrated GPU, the onboard video does this for you
- vSphere HCL Support: Really? Yep, most of the components on this mobo are on the HCL and Gigabyte lists ESXi 6 as a supported OS, its not 100% HCL but for a white box its darn close
- Full 16x PCIe Socket: Goes right into the CPU << Used for the Infiniband HCA
- Full 8x PCIe Socket: Goes into the C232 << Used for the IBM M5210
- M.2 Socket: Supporting 10Gb/s for SSD cards
- 4 x SATA III ports (white)
- 2 x SATA III can be used for Satadom ports (orange) with onboard power connectors
- 2 x Intel i210 1Gbe (HCL supported) NICs
- E3 v5 Xeon Support
- 64GB RAM Support (ECC or Non-ECC Support)
- 1 x Onboard USB 2.0 Port (Great for a boot drive)
Dislikes: (Very little)
- Manual is terrible
- Mobo Power connector is horizontal with the mobo, this made it a bit tight for a common case
- 4 x SATA III Ports (White) are horizontal too, again hard to seat and maintain
- No Audio (Really not needed, but would be nice)
- For some installs, it could be a bit limited on PCIe Ports
Some PICS :
The pic directly below shows 2 windows: Window 1 has the large Gigabyte logo, this is the headless environmental controls. From here you can control your host and launch the video viewer (window 2). The video viewer allows you to control your host just as if you were physically there. In windows 2 I’m in the BIOS settings for the ESXi host.

This is a stock photo of the MX31-BS0. It’s a bit limited on the PCIe ports, however, I don’t need many ports as soon I’ll have 20Gb/s InfiniBand running on this board but that is another post soon to come!

If you like my ‘no-nonsense’ blog articles that get straight to the point… then post a comment or let me know… Else, I’ll start writing boring blog content.
DCUI from ssh for vSphere 6 — so awesome!
This is one of those great command line items to put in your toolkit that will impress your co-workers. I think this command is one of the least known commands but could have a huge impact on an admins ability to manage their environment. The vSphere command is simply ‘dcui’ and it is a very simple way to access the DCUI without having to go into your remote IPMI tools (ilo, iDRAC, KVM over IP, etc). The only down side compared to IPMI tools is it doesn’t work when you reboot your system as you’ll lose your ssh session.
How to use it:
- After your server is fully booted, start an ssh session to your target server and logon
- From the command prompt type in dcui and press enter
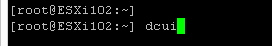
- From there you can use the dcui remotely.
- Press CTRL + C to exit

Tips:
- Have your ssh screen size where you want it prior to going into the dcui. If you resize after connecting it will exit out of the DCUI
- The DCUI command worked great in putty but it did not work with the MAC Terminal program. Not sure why, but if you got this working on a MAC then post up!
If you like my ‘no-nonsense’ blog articles that get straight to the point… then post a comment or let me know… Else, I’ll start writing boring blog content.
Using VMware Fusion for your VM Remote Console
These last few months I’ve been working to totally rebuild my Home Lab and I ran into a neat feature of Fusion. This blog article is a quick tip on using Fusion for your VM Remote console.
Issue – When you want to start a remote console to your VM’s typically you download and install VMRC (VMware Remote Console) service. Sometimes getting it to run can be a bit of a burden (Normally an OS issue).
Observation – While on my MAC I was setting up a VM via the Web Host Client and I need to mount an ISO. When I right clicked on the VM I choose ‘Launch Remote Console’ vs. the normal ‘Download VMRC’
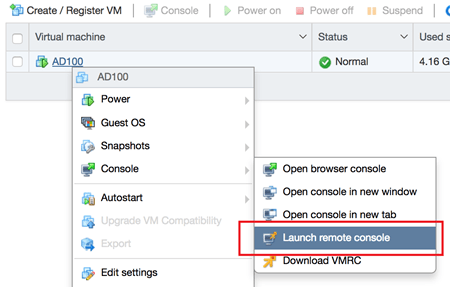
After clicking I was prompted to choose Fusion
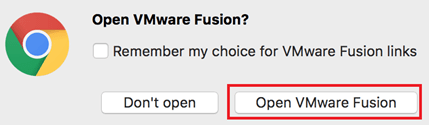
And there it was… a simple way to work with VM’s via Fusion! From there I mounted my ISO and started the rebuild of my home lab.
If you like my ‘no-nonsense’ blog articles that get straight to the point… then post a comment or let me know… Else, I’ll start writing boring blog content.
Honeywells Next Generation Platform powered by Dell FX2 and VMware vSAN
I wished over these past years I could blog in technical detail about all the great things I’ve experienced working for VMware. A big part of my job as a VMware TAM is being a trusted advisor and helping VMware Embedded OEM Partners build products they can resell to their customers. These past years I’ve worked directly with Honeywell Process Solutions to build a better offering. The entire team (Honeywell, Dell, and VMware) have been working tirelessly to make this product great. It’s been a long haul with so many late nights and deadlines but we were all proud to see this product be released.
The Honeywell Dell VMware Solution I helped Honeywell to create went on to win multiple awards.
- 2016 VMware award for OEM Partner Innovation
- 2017 TAM Customer award for Emerging Technology & Trends
- Q4-2017 Americas Co-Innovation
- 2018 WWKO ‘Best Co-Innovation’ Global Accounts
Just before VMworld 2017 Michael Dell tweeted about the great work we had all accomplished and released a video.
Passed VMware Certified Professional 6 – Data Center Virtualization Delta Exam 2V0-621D
I passed my VCP 6 – DCV Delta Exam today! Here are some of my notes around it.
- The test was 65 Questions and you have 75 Minutes to complete it, I had about 30 Mins left.
- I did get several configuration maximum questions. The questions were more around applying the known maximums vs. just memorizing the data points.
- I did get some Virtual SAN , vROPS, and LOTS of questions around Lockdown mode
- Know your licensing Models and what features belong to what.
- Lots of questions around iSCSI, FCoE, APD, Path loss, PSP Modes
- Know all about SSO, Authentication types, and don’t forget those newer features like Content Library
- Make sure you review vSphere Replication and those always fun resource pools
- Know your command line tools – esxcli and the like
- In general, questions seem to be straight to the point vs. lengthy paragraphs
- I followed the blueprint, read my documents, and made sure I read every ‘Note’ section
- For more information about this test click here

